4 New Cybersecurity Threats to Watch Out For
The speed of innovation has always been one of the true miracles of our time, but along with it come great challenges in enterprise security. According to Techjury, 30,000 websites are hacked daily, and 95% of the time, it’s due to human error. Though there will always be risks associated with technology, staying informed is vital to protecting your data from malicious actors.
In today’s article, we’ll shed light on four emerging cyber threats that IT professionals should know about:
- PureCrypter malware (targets government organizations with ransomware)
- PlugX Trojan (camouflages as Legitimate Windows Debugger Tool)
- ChromeLoader Malware (targets Gamers through fake Nintendo and Steam Games)
- RIG Exploit Kit (infects businesses through Internet Explorer)
These threats are poised to wreak havoc by taking control of networks and manipulating unsuspecting users into unwittingly divulging sensitive data. Therefore, it’s critical to understand how they work.
PureCrypter Malware
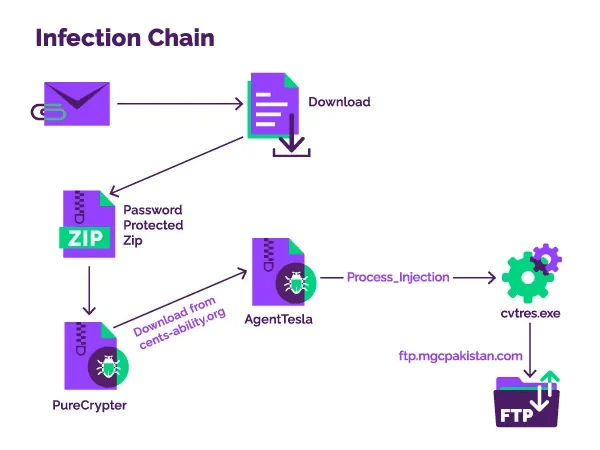
PureCrypter is a .NET-based malware downloader first detected in early 2021. It resurfaced in recent attacks targeting government entities in Asia-Pacific and North America. Threat actors are using a combination of techniques, such as process hollowing and XOR encryption, which protects communications with the Command & Control server. In their efforts to study this threat, Menlo Security researchers analyzed an AgentTesla sample, which is a keylogger that has been active since 2013 and has seen a recent activity peak in late 2020 and early 2021. The researchers have determined that it delivers the stolen data to a Pakistan-based FTP server. Since email is a key distribution methods, it is critical to stay vigilant when dealing with emails, even those originating from members of your organization.
PlugX Trojan
PlugX is a post-exploitation modular implant that has been observed masquerading as the open-source Windows debugger tool x64dbg in recent attacks. It is known for its multiple functionalities, such as data exfiltration and the ability to use the compromised machine for nefarious purposes. Attackers leverage DLL side-loading technique to load malicious DLL from a digitally signed software application and plant rogue payloads.
This allows them to fly under the radar, maintain persistence, escalate privileges, and bypass file execution restrictions. In a recent analysis, Trend Micro revealed the use of x32dbg.exe to deploy a backdoor and collect system information. Cybersecurity professionals should remain vigilant and monitor all elements of their systems for any suspicious activity related to PureCrypter or other malicious threats.
ChromeLoader Malware
ChromeLoader is a malicious software, also known as Choziosi Loader or ChromeBack, that has the capability to steal data, deploy ransomware and commit fraudulent clicks. It is primarily spread through virtual hard disk (VHD) files rather than ISO optical disc image format. The filenames used are designed to disguise VHD files as hacks or cracks for popular games on Nintendo and Steam platforms. Evidence suggests that this malware targets users looking for pirated software and video game cheats.
RIG Exploit Kit
RIG Exploit Kit is an exploit-as-a-service that was released in 2014 and is now executing close to 2,000 intrusions every day with an approximate success rate of 30%. Through targeting outdated Internet Explorer vulnerabilities such as CVE-2021-26411, CVE-2016-0189, and CVE-2019-0752, RIG EK has been observed to distribute various malware families, including Dridex, SmokeLoader, and RaccoonStealer. Information stealers are the main payloads being spread by the kit, with Dridex being the most prominent of them. However, with Microsoft planning to retire Internet Explorer in February 2023, the effectiveness of this exploit kit will soon start to decrease. Nevertheless, security professionals are urged to take appropriate measures as quickly as possible in order to stay protected from potential malicious activities enabled by this particular tool.
These threats demonstrate a small fraction of the ever-evolving strategies that cybercriminals use to evade detection and spread infection. To protect yourself against them, always treat any unexpected email content with suspicion, avoid clicking intrusive links or ads, and keep your operating system updated at all times. Check out our latest cybersecurity best practices and ensure your organization is caught on and well-protected.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

