The Rackspace Mayhem: What to do if Your Hosted Exchange Server is Breached
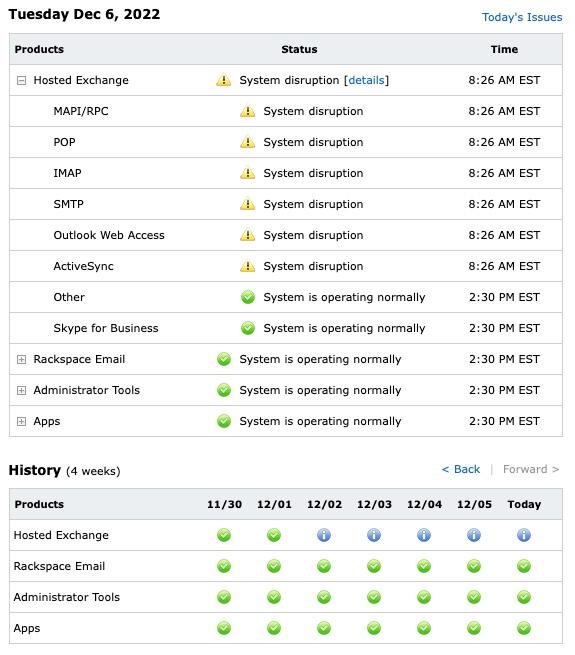
Today marks the fourth day of Rackspace Technology’s hosted Exchange Servers outage. This morning, Rackspace announced that they are working with a leading cyber defense firm to investigate the incident alongside their internal security team. The incident started on Friday, December 2, when users experienced errors while accessing the Outlook Web App (Webmail) and syncing their email clients. “We proactively powered down and disconnected the Hosted Exchange environment while we triaged to understand the extent and the severity of the impact” Rackspace stated. “After further analysis, we have determined that this is a security incident.”
A data breach is a serious security event in which sensitive, confidential, or protected data is accessed and/or disclosed without authorization. Even for businesses that have taken steps to secure their data, breaches remain a very real threat. The mayhem at Rackspace is a prime example of what an organization endures when falling prey to a breach. Concern has been growing rapidly among Rackspace users regarding their sensitive data, with no clear resolution on the horizon. Although not every breach makes headlines, incidents have been consistently rising. In 2021 alone, there were 100,000 Exchange Server breaches.
What We Know So Far
Rackspace’s investigation revealed that this incident was unique to its Hosted Exchange business. All other services are not affected and remain fully operational. Additionally, the company’s Email product line and platform have not been impacted. “We became aware of suspicious activity and immediately took proactive measures to isolate the Hosted Exchange environment to contain the incident. We have since determined this suspicious activity was the result of a ransomware incident”, Rackspace stated in a report update.
Rackspace did not provide additional information on the nature of the vulnerability that the threat actors exploited. However, security researcher Kevin Beaumont stated in a TechCrunch blog post that Microsoft Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082 may have been the target exploits.
These vulnerabilities, also known as ProxyNotShell, were first detected in late September by Vietnamese cybersecurity company GTSC and were linked to a state-sponsored attack in October, according to Microsoft.
Despite the measures that Rackspace has taken, the incident continues to interrupt its Hosted Exchange business, leading to a potential loss of revenue for its $30 million-dollar Hosted Exchange business. In addition, Rackspace Technology may suffer additional costs related to its remediation efforts.
What’s Next?
In a website-wide banner, Rackspace announced that as soon as they determine which sensitive information was affected, they will notify customers. To mitigate the damages, the company has been assisting customers in deploying replacement Microsoft 365 accounts to enable users to continue sending and receiving emails.
“At this time, moving to Microsoft 365 is the best solution for customers, and we highly encourage affected customers to move to this platform” Rackspace stated. “Since our last update, we have been able to successfully restore email services to thousands of customers on Microsoft 365.”
If your hosted Exchange server is breached, there are a few steps you need to take immediately to lessen the damage and protect your organization’s data.
-
Notify your IT team and your hosting provider
Since a data breach can be a complex issue, it is vital to have as many qualified experts working on the problem as soon as possible. Notifying your hosting provider will also allow them to take steps to secure their systems and prevent additional breaches.
If required, begin your incident response procedures, and examine any privacy responsibilities that may arise from the incident. Organizations protected by cyber insurance should contact their insurers to get further assistance.
-
Identify your system’s vulnerabilities and patch them
All users of the hosted Exchange Server are advised to investigate which vulnerabilities may affect their systems. Some of the most recently discovered vulnerabilities are outlined here. If your system has not been recently updated, take the time to install the necessary patches immediately. Note that this action is preventative and will not resolve a current compromise. Nevertheless, it is an essential part of a comprehensive security strategy and worth keeping in mind.
If you suspect that your system is compromised, follow this guide by the Microsoft Threat Intelligence Center, to evaluate to what degree your network may have been compromised.
-
Control damages by migrating to Microsoft 365
Migrating to Microsoft 365 can help move your data to a more secure environment and back it up against potential deletion. Rackspace asserts this in all its communications with affected customers. The company has also admitted that migration to Microsoft 365 may not be a silver bullet but remains the best course of action so far.
“We have heard, and understand that self-migration may not be simple and can be challenging to implement” Rackspace stated. To help its users, the company began rerouting emails to an alternate external email address. There is currently no self-service alternative that users can leverage. Clients must submit a ticket with Rackspace to ask for the workaround and submit a full list of affected accounts.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

